After successfully running ICCDI 2018 (International Collegiate Cyber Defense Invitational) in AWS, we decided we were ready to go for the big one – PRCCDC 2019 (Pacific Rim Collegiate Cyber Defense Competition).
In 2013 we were the first regional CCDC to virtualize the competition going from a bare metal server/network infrastructure to VMware vSphere. Prior to virtualizing the competition the blue teams had physical Cisco routers and switches but in the virtualized world these were replaced by easily virtualized firewall/router products such as VYOS and eventually Palo Alto networks in 2016 when they came on as a national sponsor.
Running the competition in VMware over the last six years became old hat and we didn’t have to put a lot of thought into the infrastructure which allowed us (me) time to add more creative and exciting elements into the scenario such as the raspberry pi SCADA device last year.
For ICCDI I wrote a python script to call aws cli commands to build out the environment which consisted of one subnet and 8 servers per team. For this competition each team would have 12 server, 3 subnets, 1 Palo Alto Networks PA-100, and their own VPC. I though about using terraform but ultimately decided to use python again but this time I used boto3 rather than directly calling the aws cli and django for the front end. I was already using django for the scoring engine and competition portal so it seemed like a good choice to wrap them into one project.
After about a week or so of coding and testing the script was ready to go. It’s available at my git repository. When we ran the script we had a complete game environment in AWS consisting of:
- VPC
- 15 VPCs
- 15 VPC Peering Connections
- 15 Internet Gateways
- 15 Nat Gateways
- 15 DHCP Option Sets
- 60 Subnets
- 75 Routes in 30 Route Tables
- EC2
- 300 EC2 Instances
- 30 Security Groups
- 120 Elastic IPs
- 15 Key Pairs
- Route 53
- 180 Internal DNS Records
- 120 External DNS Records
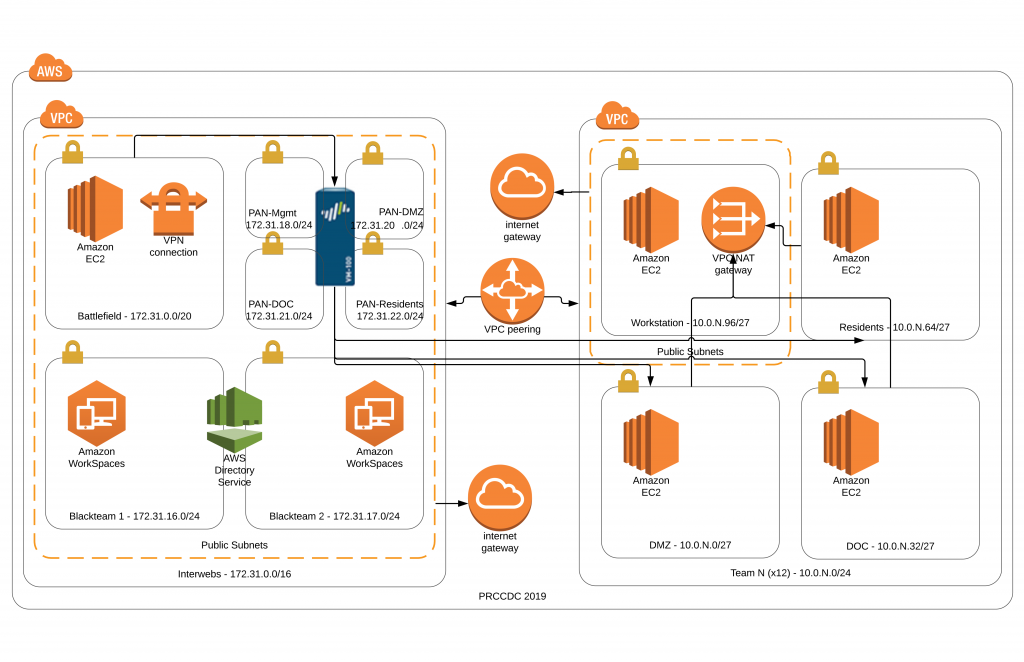
The Red Team was connected to the game environment via a VPN. In addition we also spun up 40 Kali Linux EC2 instances for the Red Team to use.
The competition was held on March 22 & 23, 2019 and despite it being our first time in AWS it was a complete success. Now that we know how to set up the infrastructure in AWS we can get back to spending out creative talents on the game scenario itself. Maybe next year the students will get their first into to containers (docker/kubernetes). Stay Tuned…